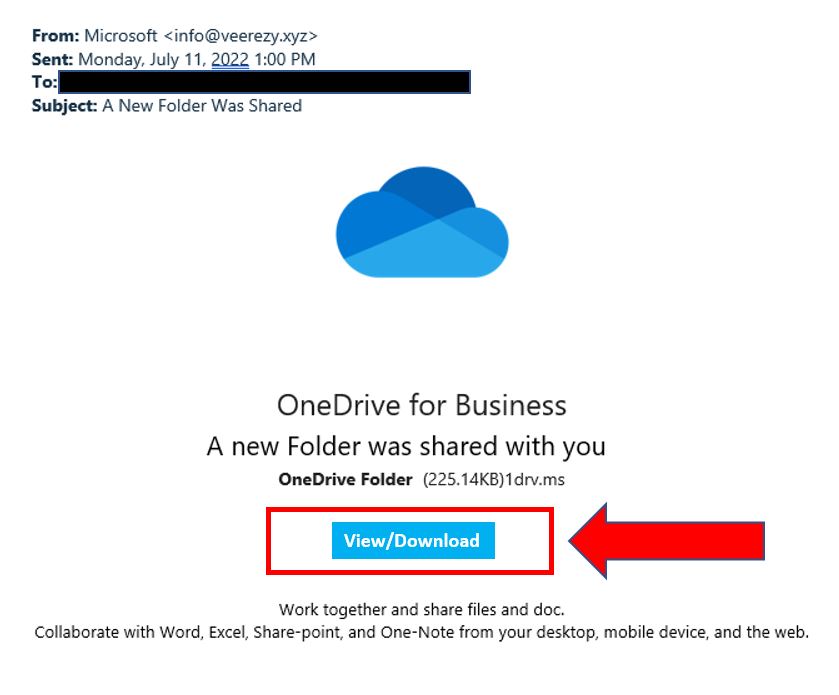
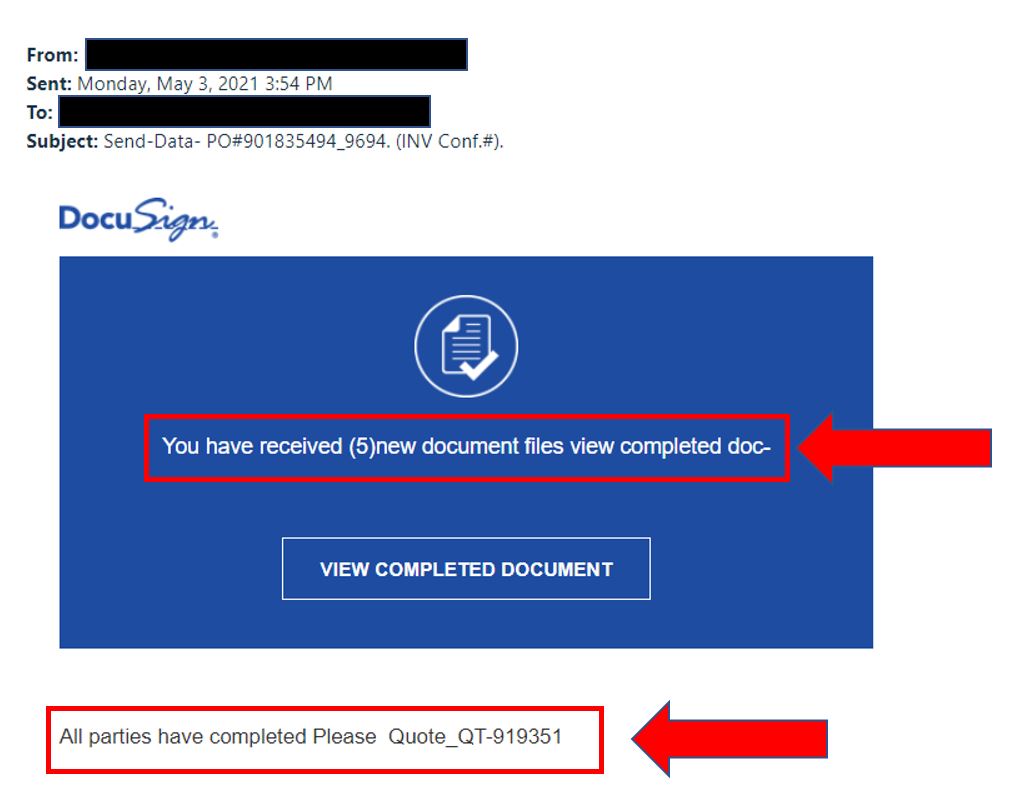
Phishing emails may contain links that direct you to a fake website that looks identical to the real one. Before clicking on any link, hover your mouse over it to see the URL (do not click, just move the mouse over it). If it looks suspicious or unfamiliar, don’t click on it. The below example show a phishing email with a tempting link (like the examples above). It also has a spoofed email address (see a pattern?).
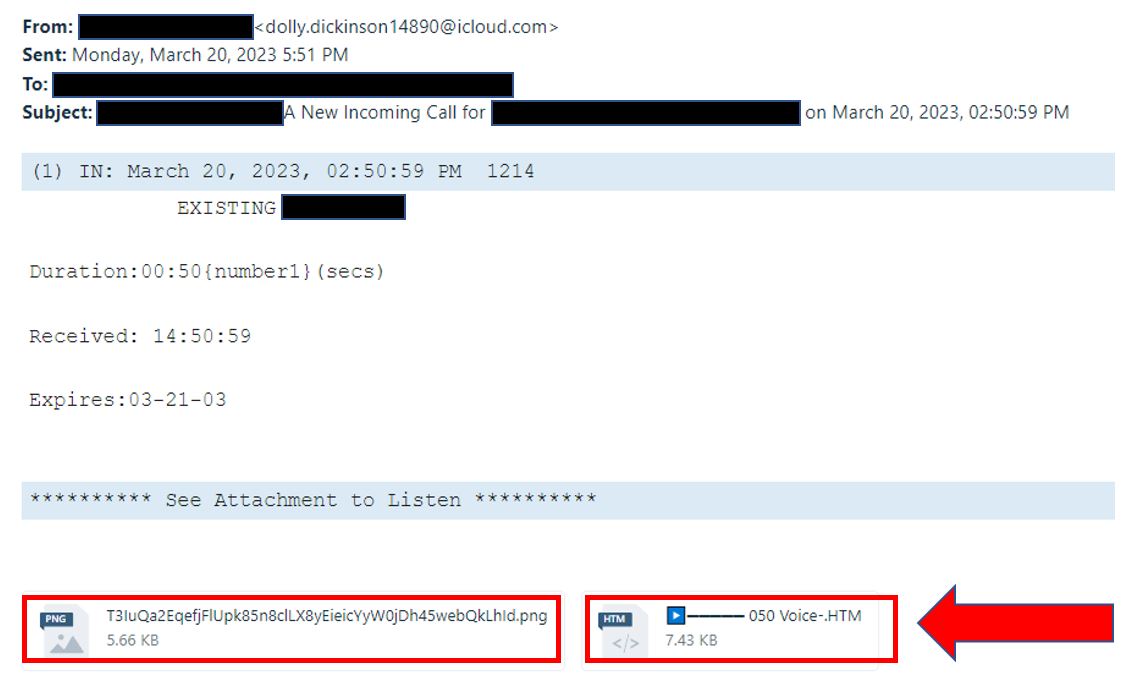
Phishing emails may contain attachments that can infect your computer with malware or viruses. Be cautious of unexpected attachments, especially if they come from an unknown sender or seem unrelated to the email’s content. If you’re not sure about an attachment, don’t open it. The below example is a phishing email made to look like a voicemail message. This is very common. You will also attachments made to look like FAXs, ACH deposits, and encrypted messages. Also be on the lookout for boobytrapped Word, Excel, and PowerPoint files (more info in another article). You can see by all the black blocks that this phishing attempt was personalized for the specific recipient. This is called spear-phishing.
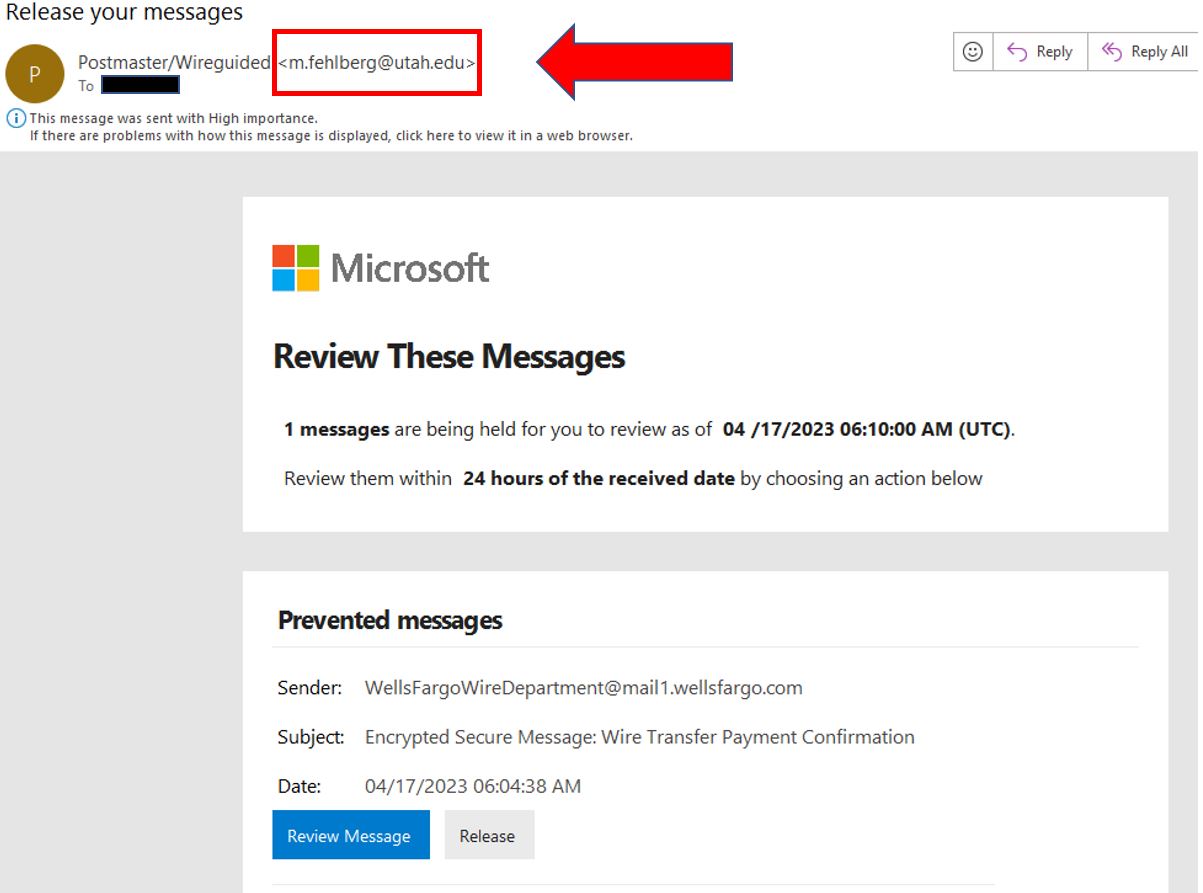
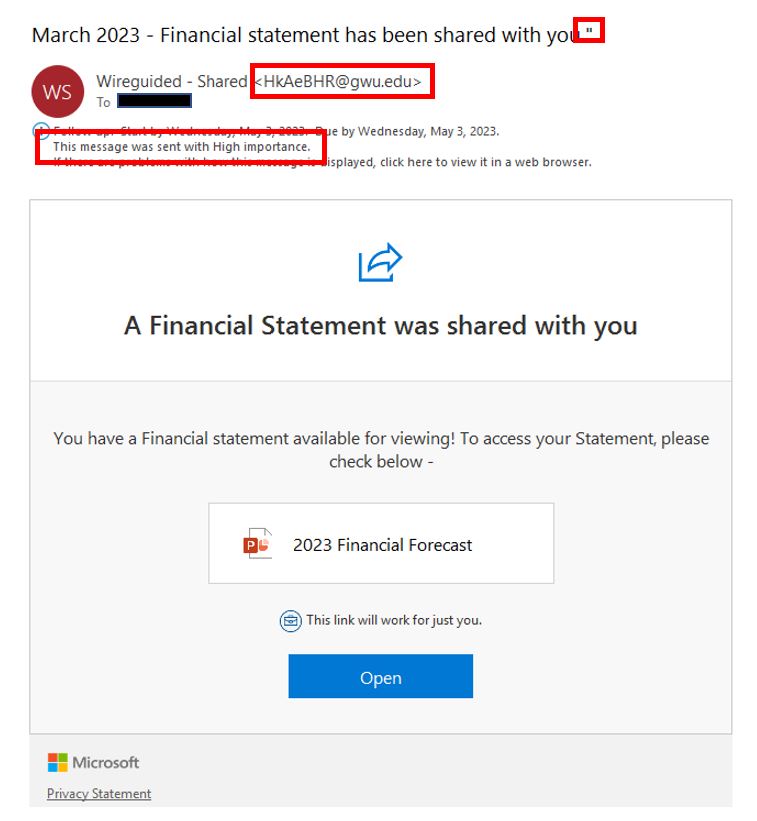
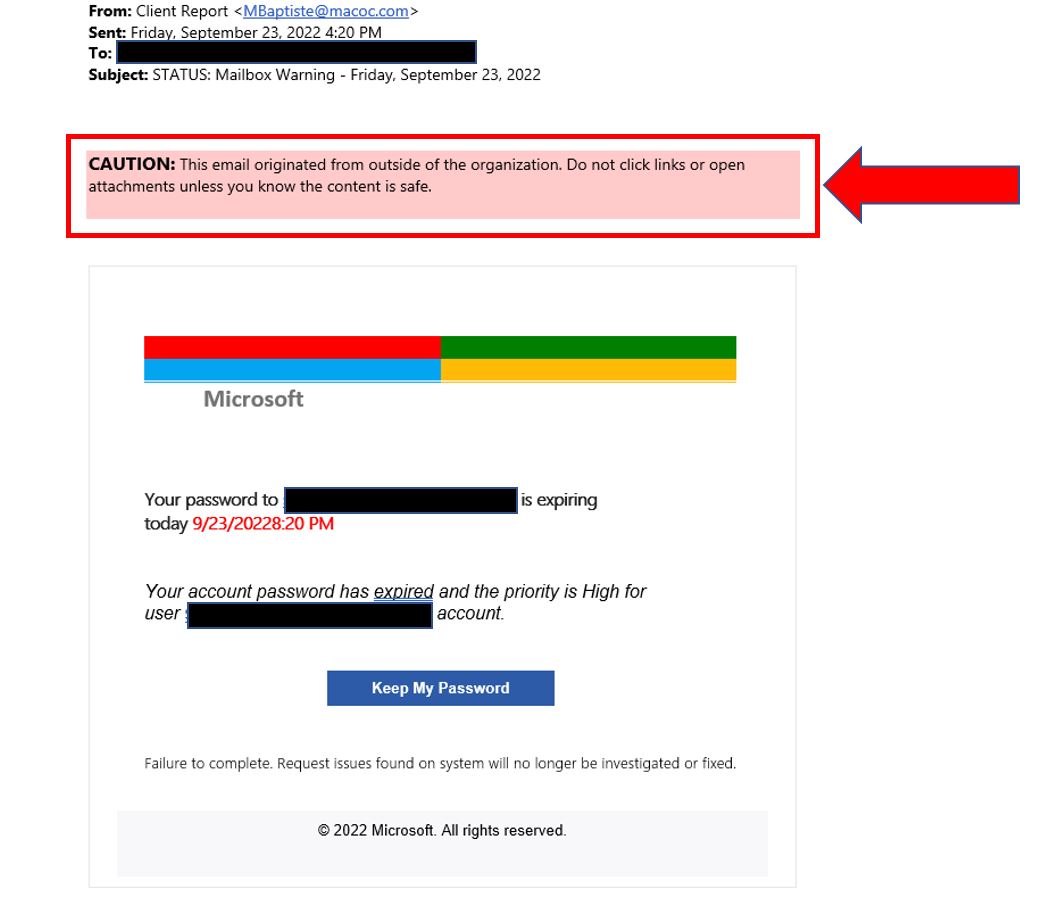
Keep an eye out for email banners that indicate the message was sent from outside the organization. Paying attention to these banners and warnings can help you identify phishing emails and protect yourself from cyber attacks. The sample below shows an example of a warning banner tipping the recipient off that this is not from their organization. It also has a spoofed email address.
Be on the lookout for poor grammar, spelling mistakes, or awkward phrasing. If an email looks like it was written by a non-native speaker or an automated tool, it’s probably a phishing attempt. With the rise of AI generated phishing emails this method of detecting phishing will lose its effectiveness.
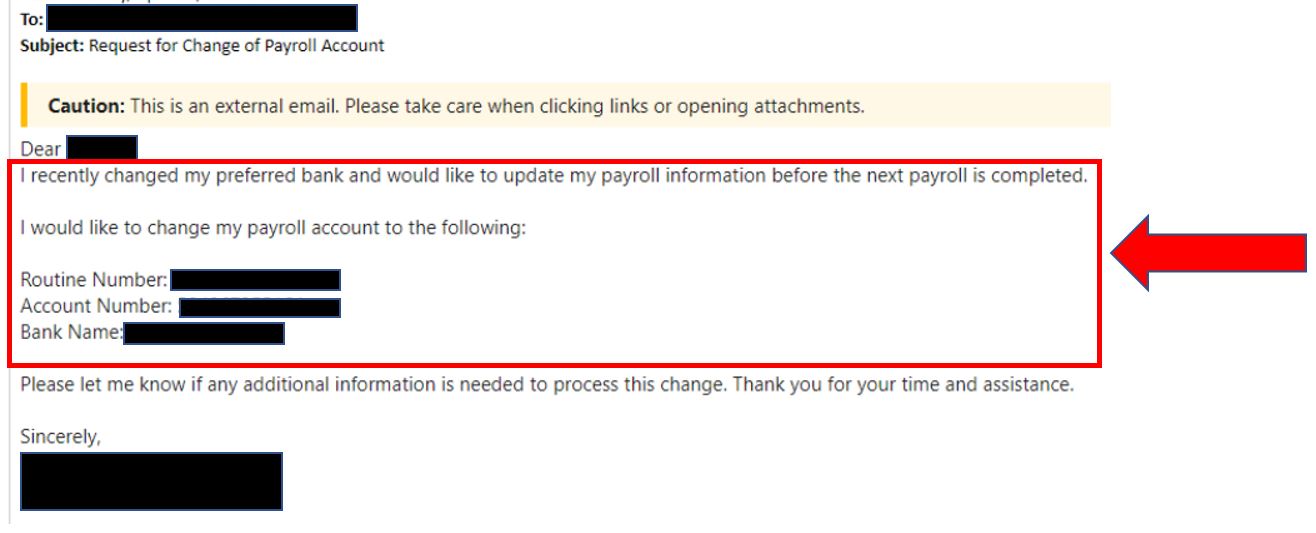
If an email asks for sensitive information like your password or social security number or wants any sort of banking information, wire transfer updates, or ACH deposits, don’t do it, even if it looks like it is coming from a co-worker as their account might be hacked or spoofed. Always verify the request by contacting the person directly by phone. Do not call any number in the email as that might be go directly to the attacker. Legitimate companies will never ask for sensitive information through email, so any request of this nature should be treated with suspicion.
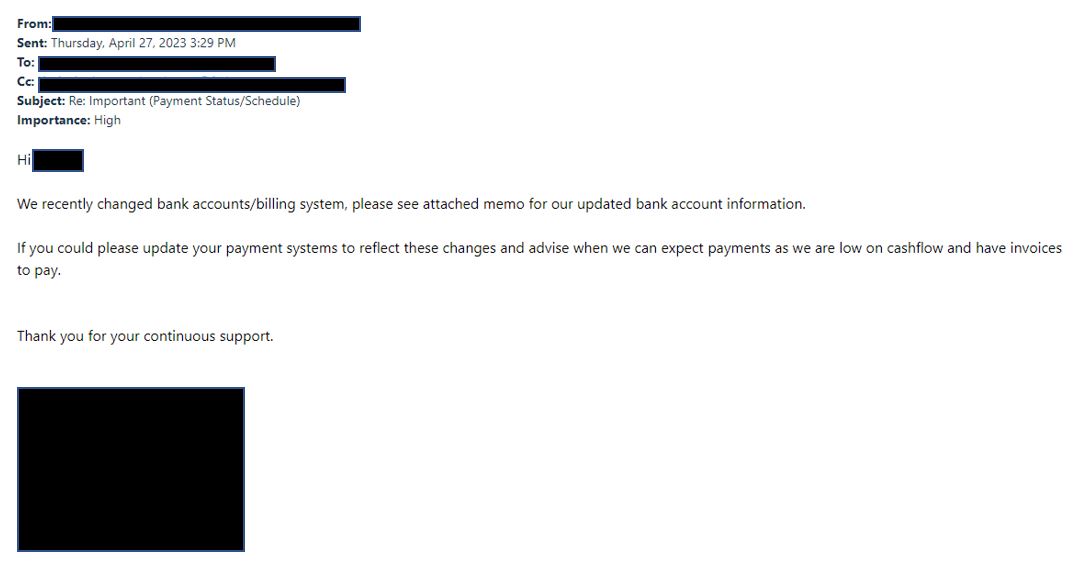
Hackers have been using a very devious tactic where they utilize a hacked company account to send emails to other employees or companies your organization does business with. Usually the message has to do with a financial transaction update such as new bank account or payroll destination. A common tactic is to hijack an existing email chain so the person you are communicating with thinks it is part of an ongoing conversation.
The below email was sent from a hacked internal account to their client. It was inserted into an ongoing conversation and the hacker redirected messages from the inbox so the victim would not see replies. The hacker waited for over a week before striking. This attack resulted in a large financial loss. To prevent this sort of attack we recommend adding a disclaimer to every message that you will never ask for financial transaction updates via email and contacting your customers directly so they know you will never email them these types of requests. Training your employees to always call and verify (not using a phone # in the email but one on file) can also prevent disaster.

 Esther Griswold
Esther Griswold Bruce DelleChiaie
Bruce DelleChiaie Andrew Hegarty
Andrew Hegarty Lisa Wollaston
Lisa Wollaston



